
Mar 07, 2022
Vivek Khanna
When organizations plan to get rid of their IT assets which has sensitive information, they need to consider disposing them by taking right recycling measures.
If recycling vendor are engaged to do this job, one thing to consider is that all recycling companies are not certified by the US Environmental Protection Agency, which means all of the data on computer could be at risk. Considering this, it is essential to use certified recycling company or use certified data sanitization software to remove sensitive information in-house. Many customers do this job inhouse to make sure all necessary steps are taken.
Importance of properly sanitizing data before recycling the IT asset
A recent study conducted by IBM and then finally completed by the Ponemon Institute shows that 25% of data breaches are attributed to negligence. This implies that users do to properly delete their sensitive data from their personal devices, like phones and computers, when they recycle them.
In 2020 alone, data breaches in United States organizations costed over $7.9 million dollars. This problem of data leakage could be prevented by having the electronics recycled properly. The right company and software product such as Jungle’s DiskDeleter can help organizations to properly wipe the memory of your electronic device so that anything that was stored will no longer be accessible.
What are among the most stolen types?
When it comes to cargo theft specifically, electronics are among the top six commodities globally. Two-thirds (66%) of these thefts happen while a cargo is in transit with 11% occurring in the warehouse. Electronics recyclers today have to consider how they will help transport equipment back to their facility securely, how to maintain security of the equipment once it arrives and again when it is prepared for further processing.’
What are top risks associated with data leakage?
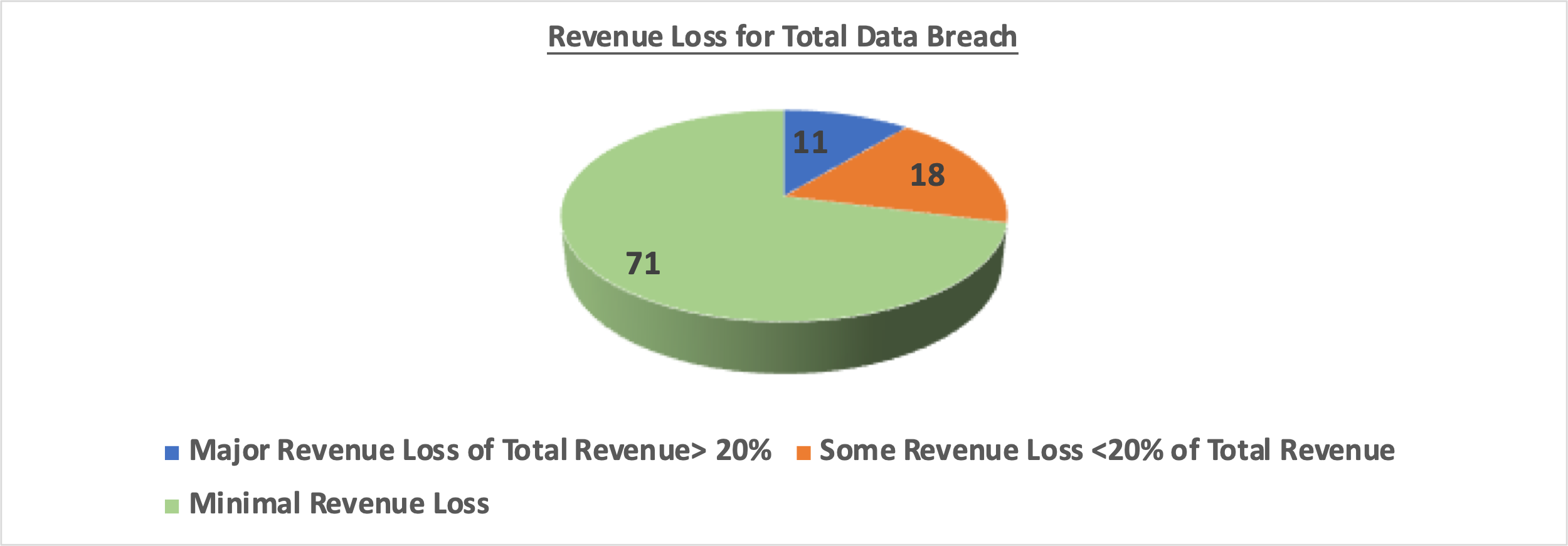
Studies show that 29% of businesses that face a data breach end up losing revenue. Of those that lost revenue, 38% experienced a loss of 20% or more for their total revenue. To put this in perspective, let’s take an example, if there are 100 companies which have data breach, 29 companies (29%) will have significant revenue loss. Out of those 38% (11 companies), will have major revenue loss which is 20% or more of their total revenue. Hence this is a serious issue with significant probability of high financial damage.
What are the main threats of data leakage?
Data breaches continue to dominate headlines around the world. Although cyber security is important to defend against cyber criminals, but proper disposal of information is equally important as that is easily avoidable problem through recommended sanitization methods.
Few risks when disposing IT assets for organizations due to data theft
- Financial Loss: The financial impact of a data leakage is undoubtedly one of the most immediate and hard-hitting consequences that organizations will have to deal with. According to a recent study by the Ponemon Institute, the cost of a data leakage has risen 12% over the past five years to £3.2m on average globally. Costs can include compensating affected customers, setting up incident response efforts, investigating the leakage, investment into new security measures, legal fees, not to mention the high regulatory penalties that can be imposed for non-compliance with the GDPR (General Data Protection Regulation).
- Reputational Damage: The reputational damage resulting from a data leak can be devastating for a business. Research has shown that up to a third of customers in retail, finance and healthcare will stop doing business with organizations that have incidence of data leakage. Additionally, 85% will tell others about their experience, and 33.5% will take to social media to vent their anger.
The negative press coupled with a loss in consumer trust can cause irreparable damage to the breached company
- Legal Action: Under data protection regulations, organizations are legally bound to demonstrate that they have taken all the necessary steps to protect personal data. If this data is compromised, whether it’s intentional or not, individuals can seek legal action to claim compensation.
There has been a huge increase in class action lawsuits in both the US and UK as victims seek monetary compensation for the loss of their data.
- Loss of Sensitive Data: If a data breach has resulted in the loss of sensitive personal data, the consequences can be devastating. Personal data is any information that can be used to directly or indirectly identify an individual. This will include everything from a name to an email address, IP address and images. It also includes sensitive personal data such as biometric data or genetic data which could be processed to identify an individual.
The reality is that if a critical patient had their medical records deleted in a data breach it could have a serious knock-on effect on their medical treatment and ultimately their life. Biometric data is also extremely valuable to cybercriminals and worth a lot more than basic credit card information and email addresses. The fallout from breaches that expose this data can be disastrous and exceed any financial and reputational damage
Organizations also need to study following security standards for best practices
- National Association for Information Destruction (NAID) AAA Certification – Global – secure data destruction industry’s standards setting and oversight body.
- Transported asset protection association (TAPA) – North America – freight security requirements standard.
- Information Security Management System (ISO 27001) – Global – relates to the recycling of e-waste, asset management involving secure data eradication and the repair and reuse of electrical and electronic equipment.
- Assured Service (Sanitization) scheme (CAS-S) – United Kingdom – scheme offered by National Cyber Security Centre for companies wishing to provide sanitization services to owners of highly classified Government data.
© 2024 Jungle KK - Powered By Knowledge Fortune

