
Data volume and the number of data storage devices have grown exponentially. This has led to the significant increase in the time required for disk sanitization, both in terms of the number of devices and data storage capacities.
A common question that IT managers ask today is: What are the best sanitization methods for each device and what are the criteria for choosing them? This article offers practical guidance for those questions.
DoD 5220.22-M (National Industrial Security Program Operating Manual) was published in 1995, which established the standard procedures and requirements for all government contractors with regards to classified information. This manual specified 3-pass overwrite for HDD sanitization and this 3-pass overwrite is often cited as DoD 5220.22-M compliant method. As it is an old standard, it does not cover new technologies such as SSD, mobile devices, etc.
Sanitization methods are now deferred to Defence Security Service, a U.S. Department of Defence (DoD) agency, and DSS manual specifies NIST 800-88 for disk sanitization.
Types of Sanitization
The NIST 800-88 Rev1 publication describes three types of media sanitization: clear, purge, and destroy, which can help ensure that data is not unintentionally released. These types are defined as follows:
- Clear: Applies logical techniques to sanitize data in all user-addressable storage locations for protection against simple noninvasive data recovery techniques; it is typically applied through the standard read and write commands to the storage device, such as by rewriting with a new value or using a menu option to reset the device to the factory state (where rewriting is not supported).
- Purge: Applies physical or logical techniques that render target data recovery infeasible using state-of-the-art laboratory techniques.
- Destroy: Renders target data recovery (using state-of-the-art laboratory techniques) infeasible and results in the subsequent inability to use the media for storage of data.
Following figure is a guide to select the best sanitization method out of these 3 types of sanitization. In short, you need to consider:
- Security level of the data stored on the device
- Whether the device will remain under or leave the organizational control
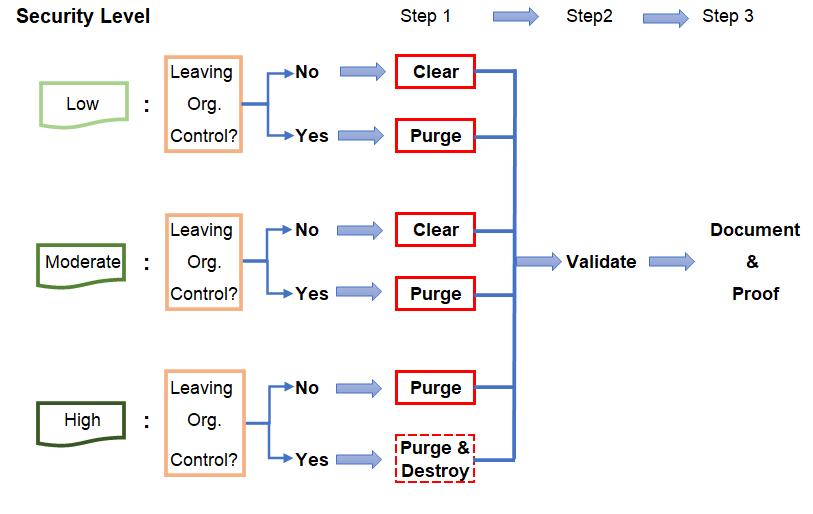
Destruction of a device has become increasingly undesirable for both environmental and cost considerations, because reliable destruction of a device requires specialized machine such as Degaussers. If destruction is being outsourced, you will need to purge data before a device leaves the organizational control.
16 methods of data sanitization DiskDeleter offers satisfy all the requirements from speedy complete data erasure to high security data purge, and completes the sanitization process all the way through documentation and proof.
For selection of a right deletion method, please see 16 Wipe Methods
Figure Source: NIST SPECIAL PUBLICATION 800-88 REVISION 1
Trends in Sanitization
The publication summarizes some trends in sanitization. For storage devices containing magnetic media, a single overwrite pass with a fixed pattern, such as binary zeros, typically hinders recovery of data. One major drawback of relying solely upon the native read and write interface for performing the overwrite procedure is that areas that are not currently mapped to active areas (e.g., defect areas, over provisioned, unallocated space) may not be securely sanitized. These native methods also may not reliably overwrite all areas when wear-leveling techniques (commonly used with flash memory, SSD) are employed.
Cryptographic Erase (CE) is an emerging sanitization technique that can be used in some situations when data is encrypted as it is stored. With CE, media sanitization is performed by erasing the cryptographic keys that were used to encrypt the stored data, as opposed to sanitizing the storage locations on media containing the encrypted data itself. However, operational use of CE today presents some challenges. In some cases, it may be difficult to verify that CE has effectively sanitized media. SP 800-88 Revision 1 describes this challenge and possible approaches.
Use of Cryptography and Cryptographic Erase
Many storage manufacturers have released storage devices with integrated encryption and access control capabilities, also known as Self-Encrypting Drives (SEDs). SEDs feature always-on encryption, which substantially reduces the likelihood that unencrypted data is inadvertently retained on the device. The end user cannot turn off the encryption capabilities which ensures that all data in the designated areas are encrypted. A significant additional benefit of SEDs is the opportunity to tightly couple the controller and storage media so that the device can directly address the location where any cryptographic keys are stored.
Cryptographic Erase (CE) leverages the encryption of target data by enabling sanitization of the target data’s encryption key. This leaves only the ciphertext remaining on the media, effectively sanitizing the data by preventing read-access. Without the encryption key used to encrypt the target data, the data is unrecoverable. Thus, with CE, sanitization may be performed with high assurance—much faster than with other sanitization techniques. This is especially important as storage devices get larger, resulting in other sanitization methods taking more time. CE can also be used as a supplement or addition to other sanitization approaches.
Critical Data Deletion Methods from DiskDeleter
DiskDeleter provides 16 of the most critical data deletion methods. You can select the best method based on your device, data confidentiality, management requirements, etc.
Deletion Methods Installed in the DiskDeleter Series:
DiskDeleter does not simply erase data. It overwrites disks using various values so that the original data cannot be restored. Following are the 16 methods used by Diskdeleter software for data sanitization.
- Zero Write
- Random Write
- NIST 800-88
- Random & Zero Write
- NIST 800-88 Advanced
- Random Random Zero
- Old US Department of Defense (DoD5200.28-M)
- US Air Force, AFSSI5020
- US Department of Defense (DoD5220.22-M)
- US Navy, NAVSO P-5239-26-MFM
- US Navy, NAVSO P-5239-26-RLL
- Bit Toggle
- German Standard: VSITR
- Peter Gutmann Secure Deletion
- Secure Erase
- Enhanced Secure Erase
Conclusion:
Several different methods can be used to sanitize media. Users should categorize the information to be disposed of, assess the nature of the medium on which it is recorded, assess the risk to confidentiality, and determine the future plans for the media. We hope this article will help users to decide which method is best. While designing DiskDeleter software, we have taken care of these highlighted data sanitization issues in this article to provide maximum compliance of standards. Our issued certificate provides all the information required for documentation in case auditors need to review the data sanitization records.
© 2024 Jungle KK - Powered By Knowledge Fortune
