
The recommended deletion process is a three-step procedure: sanitization, verification and documentation. We detailed the sanitization method in our previous blog article on data sanitization, and in this article, we will elaborate on verification and documentation.

The NIST special publication 800-88 Revision 1 recommends two types of data sanitization verification. The first method is to perform verification every time sanitization is applied.The second is a representative sampling verification, applied to a selected subset of the media. It is recommended that the sampling should be executed by personnel who were not part of the original sanitization action to avoid any potential bias. The goal of sanitization verification is to ensure that the target data was effectively sanitized. SP 800-88 Revision 1 provides different methods of verification based on destructive techniques that have been used.
Also, verification process at following levels has been recommended.
Verification of Equipment
Verification of the sanitization process is not the only assurance required by the organization. If the organization is using sanitization tools (e.g., a degausser or a dedicated workstation), then equipment calibration, as well as equipment testing, and scheduled maintenance, is also needed. In case a software like Diskdeleter is used, the software vendor can take care of this but the organization needs to make sure it is running the latest version of the software for maximum efficiency.
Verification of Personnel Competencies
Another key element of verification is the potential training needs and current expertise of personnel conducting the sanitization. Organizations should ensure that equipment operators are competent to perform sanitization functions. What we have observed is that depending upon which organizational level data sanitization is applied, there may be different personnel involved. Following are four areas where data salinization may be required and different people will be responsible.
- Server – These are normally installed in the Data Centers and when those resources are in need for data sanitization, Data Center Managers are responsible for the sanitization process.
- PCs – These are normally personal devices such as a desktop, laptop, or tablets. These are outside data centers and are in user offices or homes. Normally Desktop Managers are responsible for providing proper sanitization methods in case of disposing or reassigning the resources.
- Outsource operators – Companies that carry these tasks for an organization take this task as outsourced tasks. In this case, making sure proper verification and documentation steps are taken is very critical.
- Companies in the recycle, lease, and used device sales business – Some companies are involved in buying back the equipment and refurbish them before they are sold or recycled. When those companies are engaged, an organization needs to pay close attention on the steps suggested here.
Verification of Sanitization Results
The goal of sanitization verification is to ensure that the target data was effectively sanitized. When supported by the device interface (such as an ATA or SCSI storage device or solid state drive), the highest level of assurance of effective sanitization (outside of a laboratory) is typically achieved by a full reading of all accessible areas to verify that the expected sanitized value is in all addressable locations. A full verification should be performed if time and external factors permit. This manner of verification typically only applies where the device is in an operational state following sanitization so that data can be read and written through the native interface.
If an organization chooses representative sampling, then the following main goals apply to electronic media sanitization verification:
- Select random locations on the media each time the analysis tool is applied. This reduces the likelihood that a sanitization tool that only sanitizes a subset of the media will result in verification success in a situation where sensitive data still remains. This validation process is much faster as only subset of area is used to verify.
- Select locations across the addressable space (user addressable and reserved areas). For instance, conceptually break the media up into equally sized subsections. Select a large enough number of subsections so that the media is well-covered.
Documentation
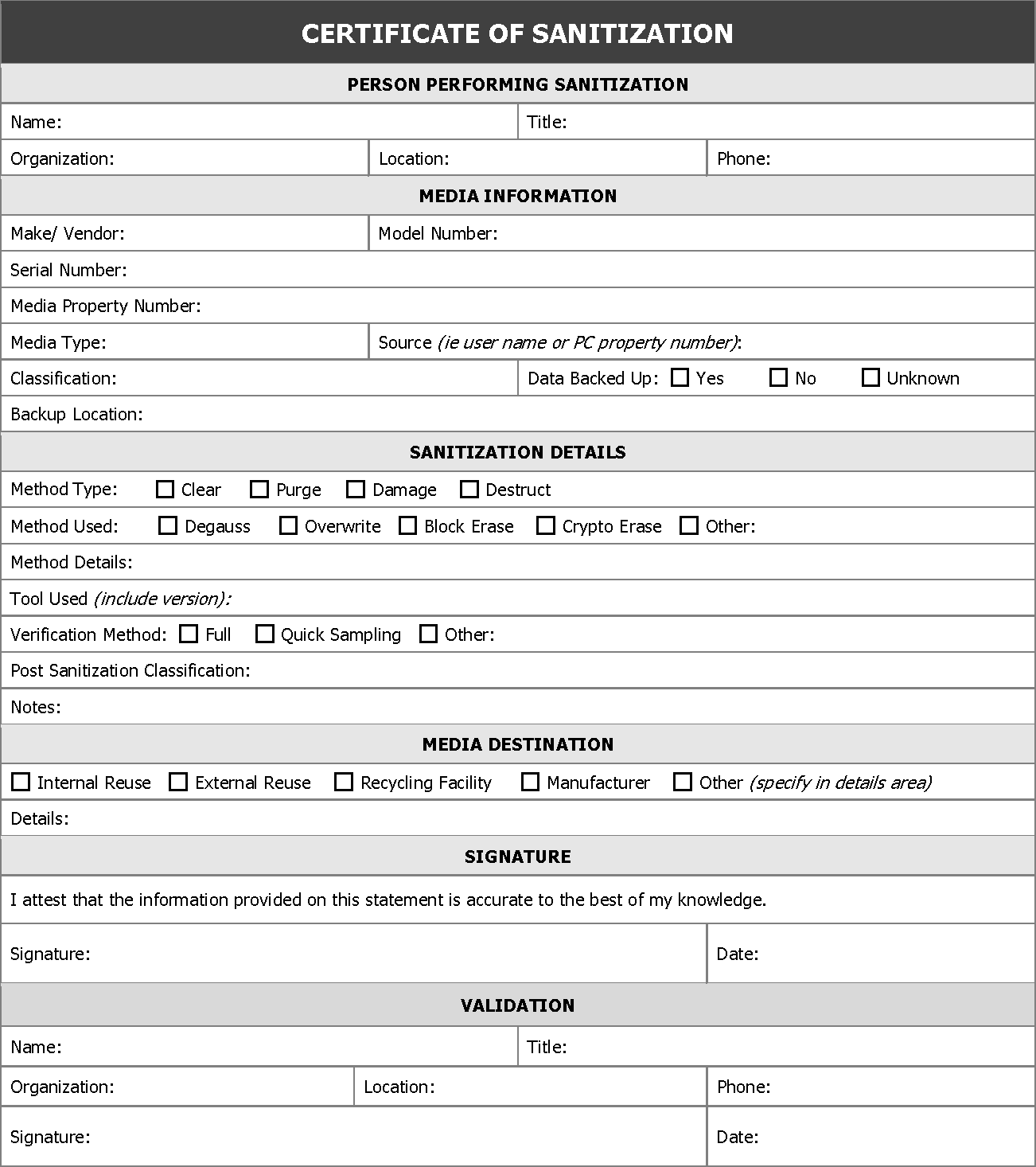
Documentation of the process is critical. Following sanitization, a certificate of media disposition should be completed for each piece of electronic media that has been sanitized. A certification of media disposition may be a piece of paper or an electronic record of the action taken. For example, most modern hard drives include bar codes on the label for model and serial numbers. The person performing the sanitization might simply enter the details into a tracking application and scan each bar code as the media is sanitized. Automatic documentation can be important as some systems make physical access to the media very difficult. The decision regarding whether to complete a certificate of media disposition and how much data to record depends on the confidentiality level of the data on the media. For a large number of devices with data of very low confidentiality, an organization may choose not to complete the certificate. When fully completed, the certificate should record at least the following details:
- Manufacturer
- Model
- Serial Number
- Organizationally Assigned Media or Property Number (if applicable)
- Media Type (i.e., magnetic, flash memory, hybrid, etc.)
- Media Source (i.e., user or computer the media came from)
- Pre-Sanitization Confidentiality Categorization (optional)
- Sanitization Description (i.e., Clear, Purge, Destroy)
- Method Used (i.e., degauss, overwrite, block erase, crypto erase, etc.)
- Tool Used (including version)
- Verification Method (i.e., full, quick sampling, etc.)
- Post-Sanitization Confidentiality Categorization (optional)
- Post-Sanitization Destination (if known)
- Data Backup (i.e., if data was backed up, and if so, where)
- For Both Sanitization and Verification:
- Name of Person
- Position/Title of Person
- Date
- Location
- Phone or Other Contact Information
- Signature of person
Below is a sample Certificate Recommended by NIST-800 publication.
© 2026 Jungle KK - Powered By Knowledge Fortune
