
Oct 19, 2022
Vivek Khanna
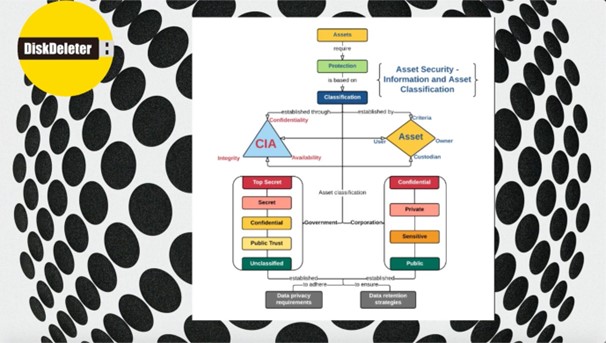
It is important for an organization to identify critical information and then design an effective security architecture and Data Sanitization process around it. Every organization should ask this question “What assets demand the best defences and protection from data leak?”
Protecting information and data has never been as vital as it is today. The initiation of stringent data protection and privacy laws such as the General Data Protection Regulation (GDPR) and ePrivacy Regulation (ePR) not only highlights the importance of data, it also raises the responsibilities for those that collect, handle, and store data. Reports of continued data breaches, despite the new policies, further reiterates this point. According to an IBM study, the cost of a data breach and leak has increased. The average cost of a data breach at US$3.86 million in 2018. Some of the major fines for violating data protection laws were, UK British Airways (fined US$230 million), Marriott (fined US$124 million), and Equifax (fined US$575 million). Each report highlights continuous threats, the costly consequences, and the importance of security and proper data disposal methods. Given these factors, organizations should make strategy to identify critical resource and then make mitigation plan. Some of the plan can be as simple as disposing the critical information properly…
What is Mission-critical Information?
Before we make a strategy of carefully disposing the information, we should decide first are we going to implement this strategy for each and every asset in organization or identify the assets which are critical (crown jewels). It is expensive and not effective way to treat all asset same so definitely identification is first step.
Different industries hold different forms of data, or the same data but held with varying degrees of importance; information assets can also take on different forms for different organizations. Here are broad classifications of information that organizations may consider as their crown jewels.
- Competitive information
- Legal information
- Personally identifiable information (PII)
- Data from daily operations
According to Trend Micro and Ponemon’s Cyber Risk Index (CRI) the top types of data at risk—R&D information, customer accounts, trade secrets, and confidential company data— fall under at least one of these categories. Cybercriminals can target their attacks on these critical resources and also those who can access this information from the recycled or disposed IT assets.
How can organizations identify their mission-critical information assets?
Each organizations must establish a definitive set of criteria or parameters for defining their mission- critical information assets. Some factors they can consider for choosing which assets to protect are the following:
Value. Data that an organization has chosen to record and store must have a finite value. Organizations should be able to quantify what value the data brings to their company and how much it influences their processes.
Risks. A good way to evaluate how important data is would be to predict the kind of threats and risks that they might inspire. Is it a sensitive or confidential data that would interest malicious actors? By answering similar questions, organizations can assess the level of risk level certain information might face and elevate its protection and create proper disposal methods.
Impact. What would be the consequence if someone steals certain information? If the impact is big enough that it cascades beyond organization borders —if it affects the safety and security of several customers, for example — then organizations should consider protecting this information as a critical asset and should be included in proper disposal of the data.
What should organizations do with their mission-critical information assets?
As recommended earlier, the first step for organizations would be to know their data better than anyone else. Following is step-step recommended steps.
Map the data. This step involves knowing what data is being collected and where all of it is being stored. In this step, organizations should also note the information generated or created by combination of different data. This gives an overview of which areas or departments hold critical data.
Identify the critical data. From the mapped data, organizations can begin to identify or perhaps revaluate their mission-critical data. This is done to prioritize security resources and identify the risk level if information is not defended or disposed properly on these assets.
Assess threats. Organizations must anticipate and recognize the possible threat actors that might target the information and assets that they hold. Also, it is a threat if the data is leaked. This can help them design and prepare defences and implementing proper data disposing and sanitizing procedures.
Plan and implement necessary data sanitization measures. Using the knowledge gathered from the first step, organizations can begin to formulate security and proper data sensitization measures to protect their critical assets and information. And a good place to start would be to ensure the sanitization of data is done at both places; At rest – when repurposed or retired and in-transit when moved, to reduce the possibility of it falling it into the wrong hands.
Overall, organizations should implement strong data sanitization and data disposal process and policies for identified mission-critical assets, preventing them frhttps://diskdeleter.com/om reaching to unwanted personnel. A software solution such as DiskDeleter (www.diskdeleter.com) can help in implementing and recording the adherence of the policies by documenting the certificates of proper sanitization for these critical IT assets. This method will be more cost effective and secure since only critical asset area of entire map of your organization, which should be top priority needs to be addressed.
© 2026 Jungle KK - Powered By Knowledge Fortune
